Exploring the Core Domains of Cybersecurity
Cybersecurity is not just about protecting systems with antivirus software. It is a vast, multi-faceted discipline involving a variety of interconnected domains, each with specific responsibilities and techniques. For students and professionals alike, understanding these core domains is essential to navigating the field and choosing a specialization.
In this post, we’ll explore the key domains of cybersecurity in depth—looking at what they involve, why they matter, and how they work together to build secure digital environments. Whether you're a student, an aspiring professional, or simply curious about cybersecurity, this guide will provide foundational knowledge to support your journey.
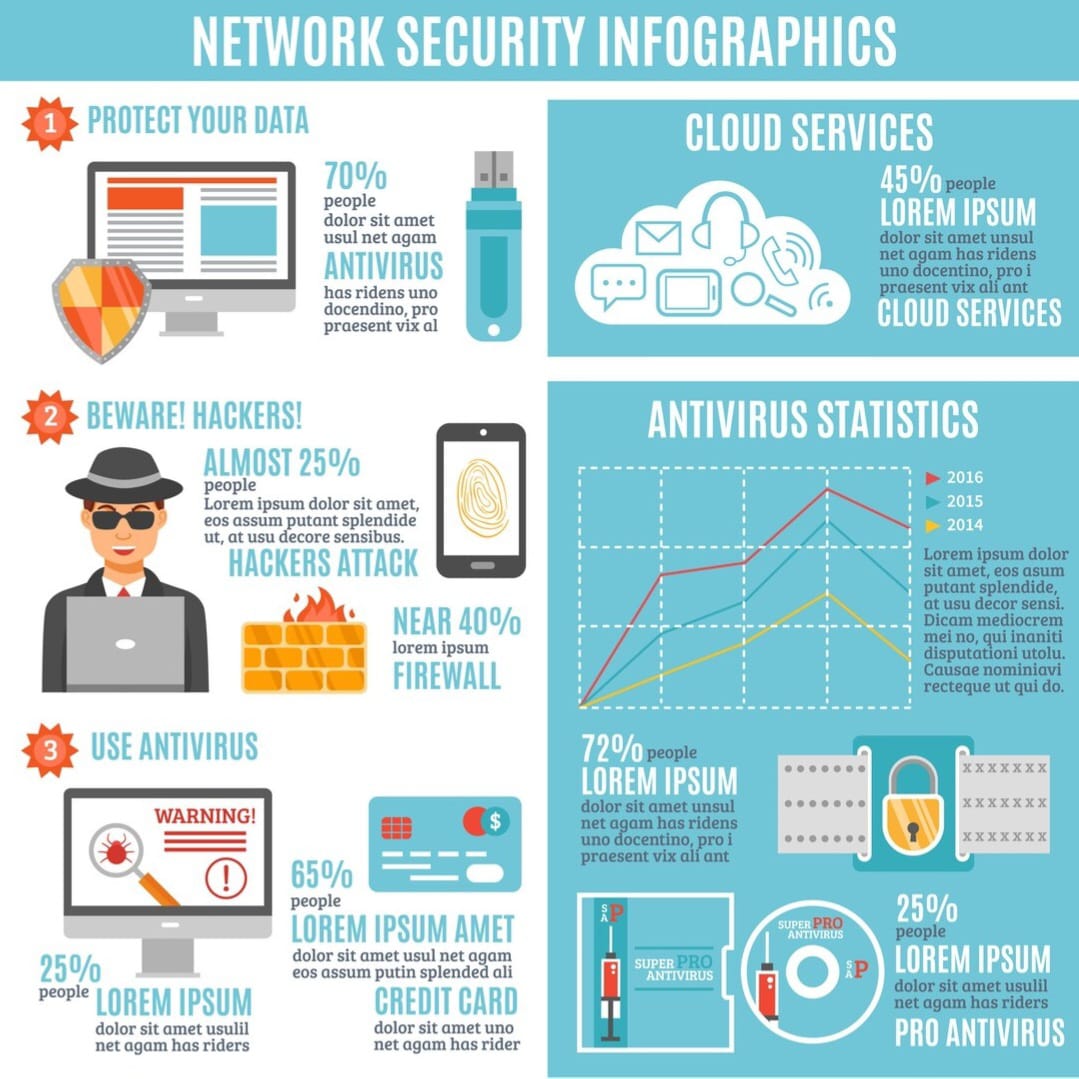
1. Network Security: Network security focuses on protecting the integrity, confidentiality, and availability of network infrastructure. This domain forms the foundation of most security strategies, acting as the first line of defense against attackers trying to access systems or data via connected networks.
Key components include:
Firewall Management: Firewalls filter incoming and outgoing traffic based on security rules. They help block malicious traffic and unauthorized access while allowing legitimate communication.
Intrusion Detection and Prevention Systems (IDS/IPS): IDS monitors traffic and alerts administrators to potential threats. IPS can take action automatically, blocking threats in real time.
Secure Network Design: This includes subnetting, segmentation, and the principle of least privilege, ensuring that even if part of the network is compromised, the damage is contained.
Remote Access Security: VPNs and secure tunneling protocols encrypt traffic from remote workers, minimizing the risk of interception.
A strong network security posture helps prevent data breaches, denial-of-service attacks, and lateral movement within a network.
2. Application Security: Application security is about securing software at all stages of development. As more services move to the web and cloud, applications become prime targets for attackers. A single vulnerability—like an exposed API or SQL injection flaw—can compromise an entire organization.
Key practices include:
OWASP Top 10: The Open Web Application Security Project maintains a list of the most critical web application security risks, such as Cross-Site Scripting (XSS), Injection flaws, and Broken Authentication.
Secure Coding: Writing code with security in mind, such as validating input, using prepared statements for database queries, and avoiding hardcoded credentials.
Penetration Testing: Simulated cyberattacks designed to uncover weaknesses in applications before real attackers do.
Code Review and Static Analysis: Systematic checking of source code (either manually or with tools) to identify insecure patterns.
Application security also includes runtime protection techniques like Web Application Firewalls (WAFs), secure DevOps pipelines (DevSecOps), and patch management.
3. System Security: System security refers to the hardening and maintenance of operating systems and endpoints. Operating systems like Windows, Linux, and macOS form the backbone of IT infrastructure, and securing them is critical.
Key practices:
Hardening: Disabling unused ports, services, and accounts. Applying group policies to enforce security settings.
Patch Management: Keeping systems up to date with the latest security patches to fix known vulnerabilities.
Endpoint Detection and Response (EDR): Tools that provide visibility into system behavior, helping detect and respond to threats.
User Account Control (UAC) and Role Management: Limiting user privileges helps prevent accidental or malicious system changes.
Misconfigured or outdated systems are among the most common attack vectors. System security ensures the underlying infrastructure is not the weakest link.
4. Data Security: Data is the most valuable digital asset. Whether it’s personal information, intellectual property, or financial records—protecting data is a top priority in cybersecurity.
Important areas:
Encryption: Data should be encrypted both at rest (e.g., stored on a disk) and in transit (e.g., being sent across a network). Algorithms like AES and RSA help secure data.
Data Classification: Categorizing data by sensitivity (e.g., public, confidential, top secret) helps apply appropriate controls.
Access Controls and Identity Management: Ensure only authorized individuals can access specific data.
Data Loss Prevention (DLP): Tools that monitor data transfers and block unauthorized sharing or leakage.
Data breaches often result in significant reputational and financial damage. Data security ensures that even if systems are compromised, the data remains protected.
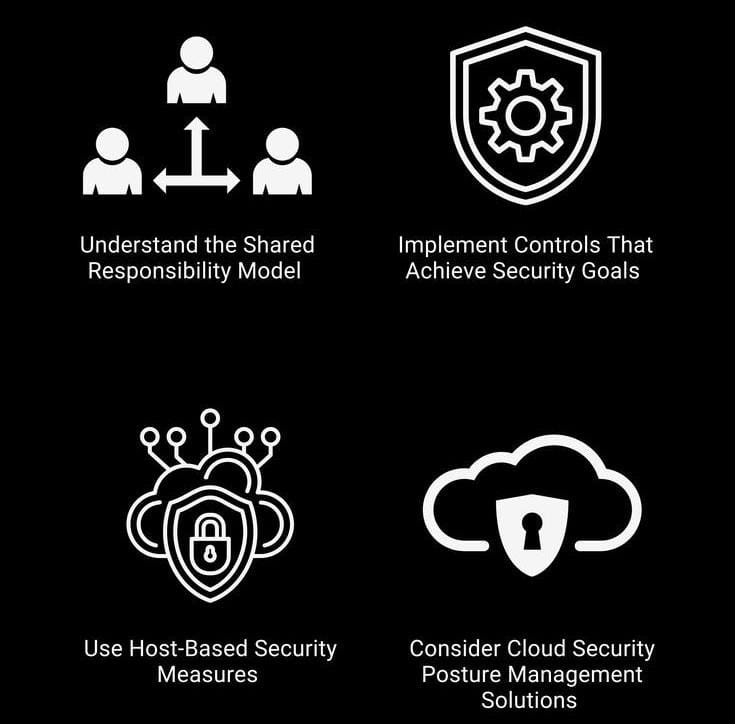
5. Infrastructure Security: Infrastructure security secures the broader IT environment—servers, cloud platforms, networking components, and support services like DNS and email.
Main focuses:
Secure DNS and Email Configuration: Misconfigured DNS or email servers can be exploited for phishing, spoofing, and malware distribution.
SIEM (Security Information and Event Management): Collects and correlates logs from across infrastructure to detect threats in real time.
Cloud Security Posture Management (CSPM): With cloud adoption rising, it's critical to manage configurations, identities, and access within cloud environments (e.g., AWS, Azure, GCP).
Zero-Day Protection: Zero-day attacks exploit unknown vulnerabilities. Infrastructure tools use threat intelligence and behavioral analysis to detect anomalies.
By securing infrastructure, organizations ensure that their platforms and services remain resilient against both internal and external threats.
6. Advanced Threat Protection (ATP): Advanced Threat Protection goes beyond traditional defense mechanisms to detect, analyze, and respond to sophisticated threats.
Key components:
Malware Analysis: Dissecting malware samples to understand their behavior, impact, and origin. Helps in developing specific countermeasures.
Sandboxing: Isolating files or apps in a controlled environment to observe behavior without risking the host system.
Threat Hunting: Proactively searching for indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) used by attackers.
Incident Response Playbooks: Predefined actions for various attack scenarios enable fast and effective responses.
ATP is essential for detecting threats that evade traditional antivirus and firewall protections, such as Advanced Persistent Threats (APTs).
7. Risk Governance & Compliance: This domain ensures that an organization’s cybersecurity efforts align with legal, regulatory, and business requirements.
Important elements:
Regulatory Standards: Frameworks like ISO 27001, HIPAA, PCI-DSS, and GDPR provide structured guidelines for managing information security.
Risk Assessments: Identify assets, threats, vulnerabilities, and the potential impact of attacks to prioritize mitigation efforts.
Audit Readiness: Keeping documentation and controls in place for internal and third-party audits.
Policy Management: Defining and maintaining security policies for everything from password rules to acceptable use policies.
Compliance isn't just about avoiding penalties—it builds trust with customers, partners, and regulators.
8. Mobile Security: Mobile devices are increasingly used for business operations, and their security risks must be addressed.
Key concerns:
App Security: Mobile apps must be tested against OWASP Mobile Top 10 vulnerabilities, including insecure data storage and improper session handling.
Mobile Device Management (MDM): Centralized tools to enforce security settings, remote wipe, and monitor device activity.
BYOD Risks: Bring Your Own Device policies must be carefully managed to separate personal and work data securely.
Rogue Access Points: Detecting and mitigating fake Wi-Fi networks that intercept mobile communications.
Mobile security ensures both corporate and personal devices stay protected in dynamic, on-the-go environments.
Conclusion Cybersecurity is a complex, ever-evolving ecosystem. Each domain—whether it's focused on securing data, preventing breaches, or aligning with global standards—plays a vital role in building a resilient security posture.
For students, understanding these domains opens the door to specialization. For professionals, it supports collaboration across teams and helps in making informed decisions. Mastering the basics of each area is the first step toward becoming a skilled cybersecurity practitioner.
Stay curious. Keep learning. The digital battlefield is always changing, and the best defense is a deep, adaptable understanding of its terrain.
#CyberSecurity #InfoSec #PenTesting #NetworkSecurity #ApplicationSecurity #Compliance #CyberAwareness #CyberCareer #SecurityOperations








Comments
Post a Comment